My friend Rich and his brothers Jared and Chris have started a really great blog that deals with Active Directory and Microsoft technologies. I highly recommed adding this blog to your reading list or favorite RSS reader.
http://cbfive.com/blog/
They already have a good number of entries up so enjoy and I'm sure you will agree that Rich, Jared, and Chris have done a really great job.
Congrats CB5!!!
Thursday, November 12, 2009
Thursday, October 22, 2009
My Friend Wrote a Book
This is one of my non-technical posts...I know I know I need some current tech content...coming soon I promise :)
I have a biological brother very close in age but growing up I also had another really good friend that I considered (and still consider) to be just as much of a brother to me.
He wrote a book this year about the journey of his family and specifically a small town called Howardsville
Kevin JOB WELL DONE!! I know this was something you have wanted to do for years. It is a huge accomplishment to write a book. I have issues writing blog entries and you finished an entire book!!
The book is called HOWARDSVILLE: The Journey of an African-American Community in Loudoun County, Virginia
The local newspaper also wrote an article about the book earlier this year
Article on Howardsville and Kevin's book
A few things not mentioned in that article. They do mention Kevin's Uncle Richard. What they don't mention there is that Richard never made the trip home from Vietnam. He made the ultimate sacrifice for our country. I didn't realize growing up what a big deal that was but now after serving I do know.
The author also mentioned that Kevin and I probably would not have the close friendship if we would grown up in a different era. That is probably true and it is a shame that it was like that for so many years but I really think things are changing for the better. We still have a ways to go but progress has been made.
I can still remember in high school having the most honest discussions about race and it really opened my eyes. I'm definitely a better person for having Kevin as a friend/brother all these years.
So Kevin time for you and the family to move back from Bermuda :)....again Great Job on the book and when do I get a signed copy hahaha
...ok back to thinking about technical content
I have a biological brother very close in age but growing up I also had another really good friend that I considered (and still consider) to be just as much of a brother to me.
He wrote a book this year about the journey of his family and specifically a small town called Howardsville
Kevin JOB WELL DONE!! I know this was something you have wanted to do for years. It is a huge accomplishment to write a book. I have issues writing blog entries and you finished an entire book!!
The book is called HOWARDSVILLE: The Journey of an African-American Community in Loudoun County, Virginia
The local newspaper also wrote an article about the book earlier this year
Article on Howardsville and Kevin's book
A few things not mentioned in that article. They do mention Kevin's Uncle Richard. What they don't mention there is that Richard never made the trip home from Vietnam. He made the ultimate sacrifice for our country. I didn't realize growing up what a big deal that was but now after serving I do know.
The author also mentioned that Kevin and I probably would not have the close friendship if we would grown up in a different era. That is probably true and it is a shame that it was like that for so many years but I really think things are changing for the better. We still have a ways to go but progress has been made.
I can still remember in high school having the most honest discussions about race and it really opened my eyes. I'm definitely a better person for having Kevin as a friend/brother all these years.
So Kevin time for you and the family to move back from Bermuda :)....again Great Job on the book and when do I get a signed copy hahaha
...ok back to thinking about technical content
Friday, October 2, 2009
Geek Network In Europe
My friend Eric went over to Germany for a customer visit and met up with one of our friends in the AD community. Anyone that reads my blog should know and follow Florian's blog too.
Not only are these guys some of the best Active Directory guys around but really cool people and good friends.
Check out Florian's post and pictures
The Geek Network at the Volksfest
New blog posts also coming from me...been very busy lately.
Thanks
Mike
Not only are these guys some of the best Active Directory guys around but really cool people and good friends.
Check out Florian's post and pictures
The Geek Network at the Volksfest
New blog posts also coming from me...been very busy lately.
Thanks
Mike
Labels:
GeekNetwork
Monday, August 24, 2009
Extend the AD Delegation Control Wizard
I often see questions in the newsgroups about wanting to delegate control of AD. An example of this would be to delegate control of an OU for example.
Delegation is important because you don't want to just give any "admin" user domain admin rights. They key is to try and limit domain admin and other elevated rights.
There is a delegation of control wizard that is started by right clicking on the OU (I'll be using an OU for this entire blog entry example)and selecting Delegate Control

When you run the wizard you get 11 choices by default at the OU level:


Where does this list of tasks come from and can it be extended?
That list is built from a file called delegwiz.inf That file is located in the\Inf folder. In my case it is in c:\windows\inf.
That file can be modified and Microsoft has a great article that gives you a new file to use and outlines the steps required to make the modifications. That is part of their Best Practices for Active Directory Administration: Appendices
For this blog entry we will specifically use:
Appendix O: Active Directory Delegation Wizard File
As you can see in Appendix O, you copy the contents to notepad and you will replace the current delegwiz.inf file with your new file. As they point out make sure to backup your current file.
After you make the changes you will now notice that you have many more choices compared to the original 11 you got by default.

There are also more advanced ways to delegate control in AD and there are some good third party tools that are also good. Some of those methods will be covered in future blog posts.
Delegation is important because you don't want to just give any "admin" user domain admin rights. They key is to try and limit domain admin and other elevated rights.
There is a delegation of control wizard that is started by right clicking on the OU (I'll be using an OU for this entire blog entry example)and selecting Delegate Control

When you run the wizard you get 11 choices by default at the OU level:


Where does this list of tasks come from and can it be extended?
That list is built from a file called delegwiz.inf That file is located in the
That file can be modified and Microsoft has a great article that gives you a new file to use and outlines the steps required to make the modifications. That is part of their Best Practices for Active Directory Administration: Appendices
For this blog entry we will specifically use:
Appendix O: Active Directory Delegation Wizard File
As you can see in Appendix O, you copy the contents to notepad and you will replace the current delegwiz.inf file with your new file. As they point out make sure to backup your current file.
After you make the changes you will now notice that you have many more choices compared to the original 11 you got by default.

There are also more advanced ways to delegate control in AD and there are some good third party tools that are also good. Some of those methods will be covered in future blog posts.
Labels:
Active Directory
Thursday, July 30, 2009
Group Policy Recommendations
From the mailbag.
Thiago sent me an email via the blog with a question about learning more about group policy. From Thiago's email
Brian Desmond's book does have a group policy section in it and that is a good place to start. I highly recommend Brian's book to anyone that works with AD. All four books in my recommendation section are great. Brian, Laura, and Kouti's books will help everyone.
There are however some resources I'd recommend for group policy specifically because that is what Thiago asked about.
First thing I'd recommend is to have some sort of lab setup if you can. That can be as simple as a virtual DC and one workstation to start with. As you are reading and learning about group policy it helps to test and play and experiment.
BOOKS
There are a few group policy specific books and both are good. The first one I'd recomend is
Group Policy: Fundamentals, Security, and Troubleshooting by Group Policy MVP Jeremey Moskowitz
That is the 4th edition of Jermey's group policy book and at close to 800 pages you will learn about group policy.
The next book is Microsoft's Group Policy Resource Kit by Derek Melber
This one I use as a reference and it has a lot of great info too. If money is tight I'd go with Jeremy's book first.
Speaking of money being tight there are a lot of great free resources on the web that can be very helpful.
BLOGS
Microsoft's Official Group Policy Team Blog Great blog from the group policy team anyone wanting to learn group policy should have this in their RSS feeds.
The GPO Guy Blog Group Policy MVP Darren Mar-Elia's blog. Hands down Darren is one of the top group policy guru's on the planet and his blog is another must read. More to come from Darren later in this post.
Florian's Blog Florian is a Group Policy MVP from Germany and a friend. His blog deals with group policy and Active Directory. He often thinks of blog entries that no one else does. His Restricted Groups entry is the best blog on the subject on the net.
Group Policy Center Another great blog from Group Policy MVP Alan Burchill A lot of great information and his blogs contain a lot of screen shots and step by step which is very helpful when learning about group policy.
Other Great Free Resources
TechNet Virtual Labs Having a test lab is very important as I mentioned above, but if you don't have one yet there are a bunch of great group policy labs provided by Microsoft. The virtual labs are a great learning tool.
Darren Mar-Elia also has some great free Group Policy Training Videos on his site. Definitely worth checking those out.
Group Policy Mail List Run by Darren this is a list that anyone wanting to learn more about group policy should subscribe too. Some really smart group policy folks on that list. You will often see very hard problems being discussed on that list.
So that is my list, I know some may wonder where Jeremy Moskowitz's training classes are. You can find Jeremy's training info here I've seen good reviews of Jeremy's class but I've never taken it so I can't personally recommend it but if you or your company has training dollars to spend it is probably going to be worth your time and money.
So what did I miss? Any blaring omissions? Please let me know and I'm sure this will not only answer Thiago's question but it will help others.
Thanks
Mike
Thiago sent me an email via the blog with a question about learning more about group policy. From Thiago's email
"...Im planning to buy in Amazon the Active Directory Book made by Brian Desmond MVP DS ( http://briandesmond.com/ad4/ ) But I would like to have your suggestion to a book that give me a inside about AD and Group Policy....because I don't wanna keep reading that basic concepts. Want more that "how to create GPO, how GPP works, how to map drives..."
Brian Desmond's book does have a group policy section in it and that is a good place to start. I highly recommend Brian's book to anyone that works with AD. All four books in my recommendation section are great. Brian, Laura, and Kouti's books will help everyone.
There are however some resources I'd recommend for group policy specifically because that is what Thiago asked about.
First thing I'd recommend is to have some sort of lab setup if you can. That can be as simple as a virtual DC and one workstation to start with. As you are reading and learning about group policy it helps to test and play and experiment.
There are a few group policy specific books and both are good. The first one I'd recomend is
Group Policy: Fundamentals, Security, and Troubleshooting by Group Policy MVP Jeremey Moskowitz
That is the 4th edition of Jermey's group policy book and at close to 800 pages you will learn about group policy.
The next book is Microsoft's Group Policy Resource Kit by Derek Melber
This one I use as a reference and it has a lot of great info too. If money is tight I'd go with Jeremy's book first.
Speaking of money being tight there are a lot of great free resources on the web that can be very helpful.
Microsoft's Official Group Policy Team Blog Great blog from the group policy team anyone wanting to learn group policy should have this in their RSS feeds.
The GPO Guy Blog Group Policy MVP Darren Mar-Elia's blog. Hands down Darren is one of the top group policy guru's on the planet and his blog is another must read. More to come from Darren later in this post.
Florian's Blog Florian is a Group Policy MVP from Germany and a friend. His blog deals with group policy and Active Directory. He often thinks of blog entries that no one else does. His Restricted Groups entry is the best blog on the subject on the net.
Group Policy Center Another great blog from Group Policy MVP Alan Burchill A lot of great information and his blogs contain a lot of screen shots and step by step which is very helpful when learning about group policy.
TechNet Virtual Labs Having a test lab is very important as I mentioned above, but if you don't have one yet there are a bunch of great group policy labs provided by Microsoft. The virtual labs are a great learning tool.
Darren Mar-Elia also has some great free Group Policy Training Videos on his site. Definitely worth checking those out.
Group Policy Mail List Run by Darren this is a list that anyone wanting to learn more about group policy should subscribe too. Some really smart group policy folks on that list. You will often see very hard problems being discussed on that list.
So that is my list, I know some may wonder where Jeremy Moskowitz's training classes are. You can find Jeremy's training info here I've seen good reviews of Jeremy's class but I've never taken it so I can't personally recommend it but if you or your company has training dollars to spend it is probably going to be worth your time and money.
So what did I miss? Any blaring omissions? Please let me know and I'm sure this will not only answer Thiago's question but it will help others.
Thanks
Mike
Labels:
Group Policy,
Mailbag
Thursday, July 23, 2009
Find Enabled Users in the Domain Admin Group
Sorry I've been out for a while, I'm back now with a quick hitter and more entries coming...well at least I have them planned in my head :)
I often receive requests from the security group to send them all user accounts in the domain admin group. What I've found is that there are often both disabled and enabled accounts. All they want is enabled accounts.
For this quick hitter I'll use my favorite tool. ADFIND by top MVP Joe Richards
adfind -default -f "name= domain admins" member -list | adfind -bit -f "&(objectcategory=person)(objectclass=user)(!useraccountcontrol:AND:=2)" samaccountname -nodn
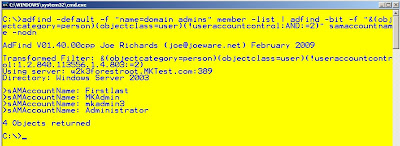
There are other ways to do that in adfind but I really love playing with adfind being piped into adfind (great feature by joe)
Can anyone see another quick hitter coming about from this...how do you do this in powershell?...what about nested groups (see previous blog entry)...more to come :)
Update from Shariq via comments
I won't be doing a quick hitter for Powershell...thanks for the assist Shariq
Get-QADgroupmember "domain admins" | Get-QADuser -enabled

I also highly recommend checking out Shariq's Blog
Thanks Shariq!!
I often receive requests from the security group to send them all user accounts in the domain admin group. What I've found is that there are often both disabled and enabled accounts. All they want is enabled accounts.
For this quick hitter I'll use my favorite tool. ADFIND by top MVP Joe Richards
adfind -default -f "name= domain admins" member -list | adfind -bit -f "&(objectcategory=person)(objectclass=user)(!useraccountcontrol:AND:=2)" samaccountname -nodn

There are other ways to do that in adfind but I really love playing with adfind being piped into adfind (great feature by joe)
Can anyone see another quick hitter coming about from this...how do you do this in powershell?...what about nested groups (see previous blog entry)...more to come :)
Update from Shariq via comments
I won't be doing a quick hitter for Powershell...thanks for the assist Shariq
Get-QADgroupmember "domain admins" | Get-QADuser -enabled

I also highly recommend checking out Shariq's Blog
Thanks Shariq!!
Labels:
Active Directory,
adfind,
quick-hitters
Wednesday, July 1, 2009
I'm a Microsoft MVP now -- Thank You

I received an email earlier today telling me that I was awarded the MVP for directory services.
This is a really great honor and something I'm very proud of. I really enjoy working in the community and more importantly I enjoy learning from others too. I obviously didn't get to this point alone so I want to take some time to thank some key people that have helped me throughout my career.
Starting back in my Army days I can't say enough and thank those that serve. One of the best things I took away from my time in the Army was some of the good friends I made. So to Daryl, Will, and Todd thank you all. You all were like brothers during my time in and I'm proud to call you friends. Additonal thanks to Todd and all those currently serving during this time of war. Hoooaaaahhh!!
I had a few internships that got me in the door but my first real job was supporting a medium size agency in DoD. I really cut my teeth there and have to single out some folks there too.
First and foremost Kevin Buckman for being a great government manager. No way I'd be where I am today without Kevin's support during those early days. Thank you Kevin!! Honorable mention to Terri C. and Jim R.
Richard Guidorizzi -- thank you Richard for the second half of my DoD career at that agency. You really helped me more than you know and always believed in me and I'll never forget what you did. Honorable mention to Leslie Butler, a great senior manager and owner of the company I worked for.
Mark, David R., Garret, and Richard(again) - the discussions that we still have to this day are really great and I learn from each and every one of you. Definitely all friends for life
A great list of admins and engineers that I worked with at DoD:
Mark, David, Garret, Larry, Greg, Lili, Cesar, Kyle, Louis, Brian T, Stuart, Steve Mc, Alex, Guy, Todd, Steve B, Matt, Jeff H, Kevin D. and last but not least Rusty. I know I missed a lot of people but thanks to everyone there. We made it through a lot there including 9/11. I can still vividly remember watching the Pentagon burn. We will always be bonded by that experience.
Thanks to Keith, TJ, Ryan, Ditter, and John at my next agency. Not the most high speed job but at least I made some good friends. Did we pause the DEN yet haha
At my current job at Unisys there are a few key people that I definitely need to thank. Mark and Eric Jansen are on the top of that list. Really enjoyed the projects I worked on with them. It is so great to work with others that are good and know their stuff. We learned from each other and I think we made a solid and real impact for the agency we supported.
Thanks to the "geek network" Florian, Eric, Mark, Rich, Dave, Brian, and Troy B. We have some good discussions and I've learned a lot from all of you guys.
Thanks to everyone at Experts-Exchange. I hang out in the Active Directory section there and I've learned a lot and hopefully helped a lot of people too. Have to give thanks to some of the other top people over there. Chris Dent, Americom, bluntTony, TigerMatt, Laura Hunter, Brandon Shell, and Brian Desmond.
Thanks to other MVPs that I have learned from for years and years. Top of that list is definitely Joe Richards. Joe is just cool as hell and knowledgeable beyond belief. His tools are a huge part of what I do. I remember the first time I emailed Joe offline and he responded with a very long and thoughtful answer. He didn't blow me off or treat me like I was a pee-on. Thank you Joe for all your work in the community. I really look forward to meeting you at the MVP summit next year.
Other great MVPs that I'd like to thank. I've met some of you in person. Others I only know via email but Thanks to: Joe, Brian Desmond, Laura Hunter, Florian F., Jorge, Mark Minasi, and Darren Mar-Elia.
Thanks to the Directory Services team at Microsoft. Ned, Rob, and everyone else that writes for the AskDS blog. Really great blogs and thanks for what you all do for the community.
Last but not least my brother Andy...thanks Andy I would not be here without you man.
I know I probably forgot people but again I didn't get here alone and I'll continue with help and support from great people.
Ok now this blog entry is starting to sound like one of those rambling Oscar speeches. The red light came on 5 minutes ago and now I'm getting the hook...I've overstayed my welcome :)
Thanks
Mike
Labels:
MVP Award
Friday, June 26, 2009
Friday 6/26 BlogRoll
I'm starting a new weekly post called the Friday BlogRoll. This is going to be some of the entries from the blog world that I found useful. It will usually be tech blogs but like everyone else in the Tech world I read other blogs too. Remember part of my blog title is "...and everything else..."
MVP Florian Frommherz had a really good entry on PDC Chaining
Really good concise explanation of what PDC chaining is and how it works. I highly recommend subscribing to Florian's blog.
The Active Directory Documentation Team has released an updated document detailing Active Directory Port Requirements
It is definitely good to know what ports are needed for AD, especially in environments where there may be firewalls and port blockages that could hinder operations. This is also where network traces and tools like portqry come in handy.
The Windows Blog team posted a blog outlining the pricing and upgrade options for Windows 7
I would have personally liked to see the prices a little lower. I understand the pricing but in these tough economic times I wonder how many people will go out and buy Windows 7. I'm guessing many will wait for their next PC that comes with Windows 7 installed. I have a feeling Windows 7 will be around 10 years from now... it is a good solid OS.
Staying on the Windows 7 theme, Microsoft has a good Windows Client Feature Comparison PDF available for download.
This is something you can give to your manager or anyone that asks what the key differences are between Windows 7, Vista, and XP.
MVP Don Jones has an ongoing 26 part series on Powershell over at Concentrated Tech.
Don has been a leader in the scripting community for years now and this is another great example of why he is one of the best around. He along with MVP Greg Shields do a great job on the Concentrated Tech site.
My brother Andy recently posted a video on YouTube about his thoughts on Twitter
Good response from the crowd at the Washington DC Improv, I could never get up and do stand up. Leave him a comment if you like the material and tell him I sent you :).
MVP Florian Frommherz had a really good entry on PDC Chaining
Really good concise explanation of what PDC chaining is and how it works. I highly recommend subscribing to Florian's blog.
The Active Directory Documentation Team has released an updated document detailing Active Directory Port Requirements
It is definitely good to know what ports are needed for AD, especially in environments where there may be firewalls and port blockages that could hinder operations. This is also where network traces and tools like portqry come in handy.
The Windows Blog team posted a blog outlining the pricing and upgrade options for Windows 7
I would have personally liked to see the prices a little lower. I understand the pricing but in these tough economic times I wonder how many people will go out and buy Windows 7. I'm guessing many will wait for their next PC that comes with Windows 7 installed. I have a feeling Windows 7 will be around 10 years from now... it is a good solid OS.
Staying on the Windows 7 theme, Microsoft has a good Windows Client Feature Comparison PDF available for download.
This is something you can give to your manager or anyone that asks what the key differences are between Windows 7, Vista, and XP.
MVP Don Jones has an ongoing 26 part series on Powershell over at Concentrated Tech.
Don has been a leader in the scripting community for years now and this is another great example of why he is one of the best around. He along with MVP Greg Shields do a great job on the Concentrated Tech site.
My brother Andy recently posted a video on YouTube about his thoughts on Twitter
Good response from the crowd at the Washington DC Improv, I could never get up and do stand up. Leave him a comment if you like the material and tell him I sent you :).
Labels:
BlogRoll
Wednesday, June 24, 2009
Find Nested Group Members
I've run into a few questions recently where someone wanted to find the members of a security group. That in itself is fairly straight forward.
However what if your security group has nested groups and users. Then those nested groups may also have additional nested groups and users. What does that query look like? How do you find all the members?
Suppose I have the following Example

There are several ways to do this, I'm not saying these are the only methods but these are three examples that work.
The first method is to use the PowerShell. For this example you will need the Quest AD Cmdlets. Thanks to MVP Dmitry Sotnikov for the Quest cmdlets.
Get-QADGroupMember "Group Name" -indirect

The second method is using ADFIND by MVP Joe Richards
adfind -default -bit -f "memberof:1.2.840.113556.1.4.1941:=DN of Group" samaccountname -nodn

More on that query here
Big Thanks to Chris Dent for that part. He was also involved in the questions. Chris was an MVP and should be an MVP again. One of the best and most knowledgeable guys around.
Now on to method three. Some people (especially in classified networks) can't install the Quest cmdlets or adfind (or any third party tool)
The Microsoft DStools can be used. For this example I'll use dsquery and dsget
dsquery group -samid "group name" | dsget group -members -expand

I hope that helps someone out there. Please let me know via comments if there are any questions.
Thanks
Mike
However what if your security group has nested groups and users. Then those nested groups may also have additional nested groups and users. What does that query look like? How do you find all the members?
Suppose I have the following Example
- TopLevelGroup -- Global Security Group
- TopLevel -- User
- TopLevel2 - User2
- Nested1 - Global Security Group
- Nested1 Members
- Nested User
- Nested User 2
- InsideNested - Global Security Group
- InsideNested Members
- InsideNested1
- InsideNested1
- Nested User
- TopLevel -- User

There are several ways to do this, I'm not saying these are the only methods but these are three examples that work.
The first method is to use the PowerShell. For this example you will need the Quest AD Cmdlets. Thanks to MVP Dmitry Sotnikov for the Quest cmdlets.
Get-QADGroupMember "Group Name" -indirect

The second method is using ADFIND by MVP Joe Richards
adfind -default -bit -f "memberof:1.2.840.113556.1.4.1941:=DN of Group" samaccountname -nodn

More on that query here
Big Thanks to Chris Dent for that part. He was also involved in the questions. Chris was an MVP and should be an MVP again. One of the best and most knowledgeable guys around.
Now on to method three. Some people (especially in classified networks) can't install the Quest cmdlets or adfind (or any third party tool)
The Microsoft DStools can be used. For this example I'll use dsquery and dsget
dsquery group -samid "group name" | dsget group -members -expand

I hope that helps someone out there. Please let me know via comments if there are any questions.
Thanks
Mike
Labels:
Active Directory,
adfind,
Powershell,
quick-hitters
Tuesday, June 16, 2009
CodePlex, a Site every AD admin should know
CodePlex is an open source project hosting website run by Microsoft. It allows shared development of open source software.
CodePlex is similar to SourceForge
There are a few key projects for the AD admin that I'd like to highlight. In future posts I'll write reviews of these products/tools. Will there be another 4/4 OU Award? :)
ADModify.NET
ADModify was created to make it easier to modify / import / export objects in Active Directory in bulk. ADModify also has a very nice undo feature if you need to back out of changes
PAL Tool
PAL is a tool that reads in a performance monitor counter log (any known format) and analyzes it using complex, but known thresholds (provided). The tool generates an HTML based report which graphically charts important performance counters and throws alerts when thresholds are exceeded. The thresholds are originally based on thresholds defined by the Microsoft product teams and members of Microsoft support, but continue to be expanded by this ongoing project.
AD Utils
AD Utils are utilities that are primarily focused on administration and operations of Active Directory.
The AD Utils include
There are many other tools and utilities on CodePlex. Please leave comments about some other good/useful tools you use for your AD and Server Administration duties from the site.
I'll be posting more information and reviews of the utilites in the future.
CodePlex is similar to SourceForge
There are a few key projects for the AD admin that I'd like to highlight. In future posts I'll write reviews of these products/tools. Will there be another 4/4 OU Award? :)
ADModify.NET
ADModify was created to make it easier to modify / import / export objects in Active Directory in bulk. ADModify also has a very nice undo feature if you need to back out of changes
PAL Tool
PAL is a tool that reads in a performance monitor counter log (any known format) and analyzes it using complex, but known thresholds (provided). The tool generates an HTML based report which graphically charts important performance counters and throws alerts when thresholds are exceeded. The thresholds are originally based on thresholds defined by the Microsoft product teams and members of Microsoft support, but continue to be expanded by this ongoing project.
AD Utils
AD Utils are utilities that are primarily focused on administration and operations of Active Directory.
The AD Utils include
- CheckDSAcls
- ReplDiag
- TrustCheck
- FindGuidInAD
- SearchForDuplicateAttributeData
There are many other tools and utilities on CodePlex. Please leave comments about some other good/useful tools you use for your AD and Server Administration duties from the site.
I'll be posting more information and reviews of the utilites in the future.
Labels:
Active Directory,
CodePlex
Tuesday, June 9, 2009
Find Users Who are Not in Specific Groups
I know everyone has been wondering what happened to the quick hitter series...well it is back :)
This question has come up twice over the last few weeks on the AD section at Experts Exchange so that means time for an entry.
The question is suppose I have some groups and I want to find out if users are not members of any of the groups.
Example:
GroupA, GroupB, GroupC, GroupD - So how do I find out what users are not members of those groups?
Two quick ways that I like to use are ADFIND and Powershell. I know there are other methods.
The first is to use ADFIND by MVP Joe Richards
adfind -default -f "&(objectcategory=person)(objectclass=user)(!memberof=DN of groupA)(!memberof=DN of groupB)(!memberof= DN of group C)(!memberof= DN of groupD)" samaccountname memberof -nodn

The other method is to use PowerShell. For this example you will need the Quest AD cmdlets. Thanks to Dmitry Sotnikov for those
get-qaduser -sizelimit 0 -notmemberof groupa, groupb, groupc, groupd | ft -wrap samaccountname, memberof

In my examples I've outputted the memberof field just so you can verify the commands do what you want and don't have users that are members of those groups, you can take that out if you want.
UPDATE: Joe Richards wrote a great blog entry about DN Formats in AD
As you can see from Joe's post you can also use the GUID of the group instead of the DN in the adfind/LDAP query.
Want to quickly find the GUID of your group...ADFIND once again :)
adfind -sc g:GroupName objectGUID
Thanks
Mike
This question has come up twice over the last few weeks on the AD section at Experts Exchange so that means time for an entry.
The question is suppose I have some groups and I want to find out if users are not members of any of the groups.
Example:
GroupA, GroupB, GroupC, GroupD - So how do I find out what users are not members of those groups?
Two quick ways that I like to use are ADFIND and Powershell. I know there are other methods.
The first is to use ADFIND by MVP Joe Richards
adfind -default -f "&(objectcategory=person)(objectclass=user)(!memberof=DN of groupA)(!memberof=DN of groupB)(!memberof= DN of group C)(!memberof= DN of groupD)" samaccountname memberof -nodn

The other method is to use PowerShell. For this example you will need the Quest AD cmdlets. Thanks to Dmitry Sotnikov for those
get-qaduser -sizelimit 0 -notmemberof groupa, groupb, groupc, groupd | ft -wrap samaccountname, memberof

In my examples I've outputted the memberof field just so you can verify the commands do what you want and don't have users that are members of those groups, you can take that out if you want.
UPDATE: Joe Richards wrote a great blog entry about DN Formats in AD
As you can see from Joe's post you can also use the GUID of the group instead of the DN in the adfind/LDAP query.
Want to quickly find the GUID of your group...ADFIND once again :)
adfind -sc g:GroupName objectGUID
Thanks
Mike
Labels:
Active Directory,
Powershell,
quick-hitters
Monday, May 25, 2009
Thank You Veterans on Memorial Day
Today is Memorial Day in the United States. It commemorates U.S. men and women who died while in service for their country.
There are no words that can truly express my feelings. We can't give enough thanks to those that have made the ultimate sacrifice. I not only give thanks to those that made the ultimate sacrifice but also to the loved ones they left behind.
I also extend my deepest thanks to our fallen allies. We don't go into battle alone and many men and women from other countries have also made the ultimate sacrifice.
I doubt anyone I served with reads an Active Directory blog but thank you to my brothers in the Army and to anyone that has served in any branch of the military. Hooaaahhh!!
There are no words that can truly express my feelings. We can't give enough thanks to those that have made the ultimate sacrifice. I not only give thanks to those that made the ultimate sacrifice but also to the loved ones they left behind.
I also extend my deepest thanks to our fallen allies. We don't go into battle alone and many men and women from other countries have also made the ultimate sacrifice.
I doubt anyone I served with reads an Active Directory blog but thank you to my brothers in the Army and to anyone that has served in any branch of the military. Hooaaahhh!!
Labels:
Army Hooaahh
Wednesday, May 13, 2009
Add Employee ID Field - ADUC
I've seen this question several times on various message boards so I wanted to write a step by step entry on how to do this.
User objects have an employeeID attribute but it doesn't appear by default in active directory users & computers.
Sakari Kouti has written a great script to help with this. You can find that script here(employeeID.vbs)
Step1:
Download the script and save it on your PC. I've put the script on my C drive in a folder called AddID
Step2:
In ADSI Edit go to the configuration container and navigate to CN=DisplaySpecifiers, CN=409)
In the right pane find CN=user-display and right click and select properties.

Step3:
Select the adminContextMenu attribute. Add the following value
2, Employee &ID, path to script
Note: If 2 is in use just pick the next number. In my example I've put the script in c:\addid\employeeid.vbs

UPDATE: I should have added this when I first posted this but thanks to Rob Sampson for pointing it out. Rob is one of the strongest scripters I've met and is a valuable member of the IT community.
From Rob (Thanks Rob!):
Screen shot below shows that example in my mktest.com domain.

Step4:
Now if you use Active Directory Users & Computers you can right click on a user and employee ID should appear.

You can select the field and edit it:

Thanks to Sakari Kouti for the script. He also has a new book coming out called Active Directory 2008 Unleashed
If that book is anything like his last book (Inside AD 2nd Edition) then it is a must have...I've already pre-orderd the new book :)
User objects have an employeeID attribute but it doesn't appear by default in active directory users & computers.
Sakari Kouti has written a great script to help with this. You can find that script here(employeeID.vbs)
Step1:
Download the script and save it on your PC. I've put the script on my C drive in a folder called AddID
Step2:
In ADSI Edit go to the configuration container and navigate to CN=DisplaySpecifiers, CN=409)
In the right pane find CN=user-display and right click and select properties.

Step3:
Select the adminContextMenu attribute. Add the following value
2, Employee &ID, path to script
Note: If 2 is in use just pick the next number. In my example I've put the script in c:\addid\employeeid.vbs

UPDATE: I should have added this when I first posted this but thanks to Rob Sampson for pointing it out. Rob is one of the strongest scripters I've met and is a valuable member of the IT community.
From Rob (Thanks Rob!):
you could place "employeeid.vbs" in your NetLogon share of a Domain Controller (which then replicates to all other DCs), and have 2. Employee &ID, \\domain.com\sysvol\domain.com\scripts\employeeid.vbs
Screen shot below shows that example in my mktest.com domain.

Step4:
Now if you use Active Directory Users & Computers you can right click on a user and employee ID should appear.

You can select the field and edit it:

Thanks to Sakari Kouti for the script. He also has a new book coming out called Active Directory 2008 Unleashed
If that book is anything like his last book (Inside AD 2nd Edition) then it is a must have...I've already pre-orderd the new book :)
Labels:
Active Directory
Tuesday, May 12, 2009
Product Review - GPO Compare from SDMSoftware
This is the first in my "product review" series. I will try and test products (free and not free)relevant to all aspects of active directory and group policy.
Today we start with GPO Compare.
GPO Compare is produced by SDMSoftware If you don't know SDMSoftware then you probably know their founder. Darren Mar-Elia is the founder and has been a long time group policy MVP and generally considered one of the best group policy guys in the business.
Currently there are no free native Microsoft tools that can be used to compare the differences between two group policies. Microsoft does make a product called Advanced Group Policy Managment (AGPM) AGPM is part of the Microsoft Desktop Optimization Pack (MDOP). MDOP is only available to software assurance customers.
Many are not software assurance customers so they are out of luck...until now.
...so let's start the review.
The first thing you will want to do is download GPO Compare. You can get it here
What I first noticed is that I had a fully functional trial. That is always nice because I didn't have any features blocked or not available.
The download is approximately 7MB and the install is super easy and fast.
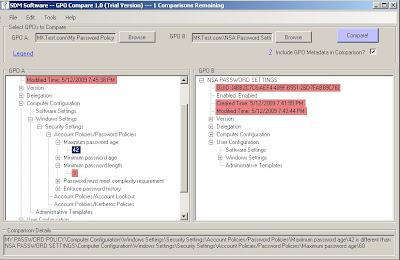
After you install and launch the program the first screen you see is self explanatory. As you can see in the screen shot below you can browse for two group policy objects (GPOs).
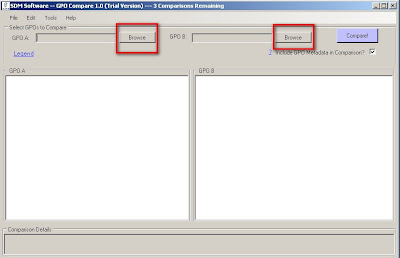
When you select Browse you will be presented with a screen that shows all the policies for your domain.
For this example I'll be using two password policies.
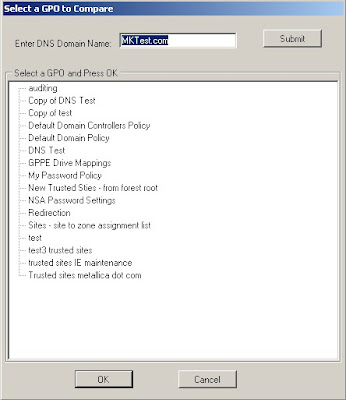
You will notice the check box labeled "Include GPO Metadata in Comparison?"
That setting/option includes comparisons of GPO metadata such as created and modified dates, security permissions and links. If the option is unchecked then those items are not included in the comparison. For this first run I'll include those items.
So for these policies for instance if I don't select it then there are only 6 differences versus 11.
...so now as you guessed it you can go ahead and select compare:
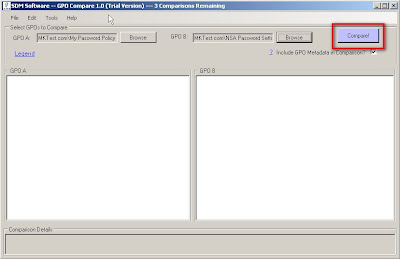
When you run the compare the first thing you will see is a box telling you how many differences there are. As you can see in the screenshot there are 11 differences between my two GPOs.
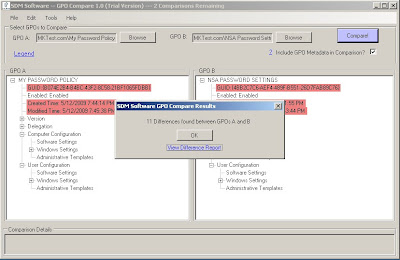
You can view the difference report from this dialogue box or you can access the report from the Tools menu.
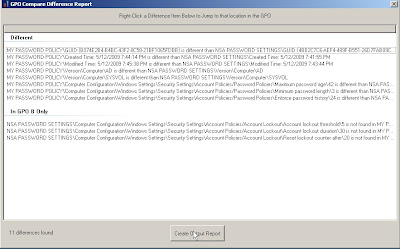
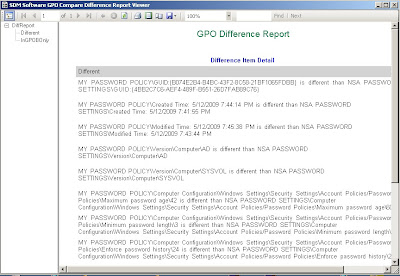
The GPO Compare Difference Report will show you the differences between the group policies.
As you can see you can also right click and jump directly to that particular setting/difference.
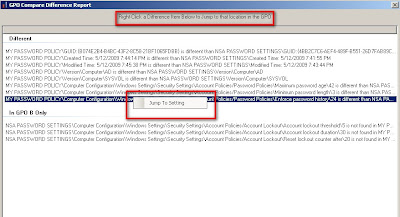
After you select "jump to setting" you will be directed back to the main page and the exact details are spelled out in the "comparision details" section
My favorite part is the GPO Difference Report that you can create. You can save it or print it. Very easy for even managers to follow :)
An example of the GPO Difference report is in the screenshot below
My overall thoughts is that this is a great tool!! It is very easy to use, the full version costs less than $100 and it really fills a much needed void in the group policy landscape.
Final Verdict = 4/4 OUs - WELL DONE!!
Today we start with GPO Compare.
GPO Compare is produced by SDMSoftware If you don't know SDMSoftware then you probably know their founder. Darren Mar-Elia is the founder and has been a long time group policy MVP and generally considered one of the best group policy guys in the business.
Currently there are no free native Microsoft tools that can be used to compare the differences between two group policies. Microsoft does make a product called Advanced Group Policy Managment (AGPM) AGPM is part of the Microsoft Desktop Optimization Pack (MDOP). MDOP is only available to software assurance customers.
Many are not software assurance customers so they are out of luck...until now.
...so let's start the review.
The first thing you will want to do is download GPO Compare. You can get it here
What I first noticed is that I had a fully functional trial. That is always nice because I didn't have any features blocked or not available.
The download is approximately 7MB and the install is super easy and fast.
After you install and launch the program the first screen you see is self explanatory. As you can see in the screen shot below you can browse for two group policy objects (GPOs).

When you select Browse you will be presented with a screen that shows all the policies for your domain.
For this example I'll be using two password policies.

You will notice the check box labeled "Include GPO Metadata in Comparison?"
That setting/option includes comparisons of GPO metadata such as created and modified dates, security permissions and links. If the option is unchecked then those items are not included in the comparison. For this first run I'll include those items.
So for these policies for instance if I don't select it then there are only 6 differences versus 11.
...so now as you guessed it you can go ahead and select compare:

When you run the compare the first thing you will see is a box telling you how many differences there are. As you can see in the screenshot there are 11 differences between my two GPOs.

You can view the difference report from this dialogue box or you can access the report from the Tools menu.

The GPO Compare Difference Report will show you the differences between the group policies.

As you can see you can also right click and jump directly to that particular setting/difference.

After you select "jump to setting" you will be directed back to the main page and the exact details are spelled out in the "comparision details" section

My favorite part is the GPO Difference Report that you can create. You can save it or print it. Very easy for even managers to follow :)
An example of the GPO Difference report is in the screenshot below

My overall thoughts is that this is a great tool!! It is very easy to use, the full version costs less than $100 and it really fills a much needed void in the group policy landscape.
Final Verdict = 4/4 OUs - WELL DONE!!

Labels:
Group Policy,
OU Awards,
Product Reviews
Saturday, May 9, 2009
Steve Riley has left Microsoft
Steve Riley was let go as part of Microsoft's restructuring...this was round two of layoffs at Microsoft.
Steve Riley was one of Microsoft's best known speakers. His concentration was security related issues. I know times are tough for all companies but I was really surprised by this news.
Security is a huge concern in most corporations and Steve was a great speaker at most major events and brought a lot to the community.
I'm sure he will do well with whatever he does next but this is a head scratcher for sure.
If you read the comments to his blog entry you will see that he will definitely be missed.
Good Luck Steve!!
Steve Riley was one of Microsoft's best known speakers. His concentration was security related issues. I know times are tough for all companies but I was really surprised by this news.
Security is a huge concern in most corporations and Steve was a great speaker at most major events and brought a lot to the community.
I'm sure he will do well with whatever he does next but this is a head scratcher for sure.
If you read the comments to his blog entry you will see that he will definitely be missed.
Good Luck Steve!!
Labels:
Microsoft News
Thursday, April 30, 2009
How do you secure Active Directory and Windows Servers?
Computer security is a big concern these days and securing your Active Directory and Windows Servers is one of the most important things we can do as admins and engineers.
I also see questions come up all the time about people wanting to know how to secure their machines.
Although there is not one answer for every environment there are some good guidelines that have been released by Microsoft and various US Federal agencies that can help out.
In my opinion there are a handful of universal rules that apply to any Active Directory environment.
UNIVERSAL RULE#1:
Limit the number of enterprise and domain administrators. I've seen plenty of organizations lock down their systems and take a lot of good security measures and then you look and there could be 50-100 (or more)domain admins.
Domain admins have control over every aspect of your domain, in fact a domain admin can have control of your entire forest.
It is important to limit these very powerful accounts. Limiting admins also limits the number of inadvertent mistakes that can cause issues
UNIVERSAL RULE#2:
See Rule #1 :)
UNIVERSAL RULE#3:
Don't give your users admin rights to their PCs. This seems like a no brainier but I was involved in a question on one of the boards recently and the admin's boss mandated that he make all the users admins on their machines.
So now you have limited admins and you have a good anti-virus program and are patching your servers with the appropriate patches.
What other guidelines are out there to help an admin secure AD and their servers?
The following is a list of some guides that should get most organizations going in the right direction
UPDATE via comments from Garrett - Thanks Garrett!!
Those guides are a really good place to start if you want to learn more about securing your Windows Servers and AD Infrastructure.
This all leads me to Universal Rule #4...
UNIVERSAL RULE#4:
Don't just blindly install security templates and don't lock down Active Directory or your servers without testing testing testing. This may seem like common sense but again I've seen many incidents of servers or AD being hardened and then users may lose functionality or other major problems can arise because the lock downs were not tested. It is important to be secure but at the end of the day it is also important for our users/customers to be able to function and do their jobs.
You say you don't have a test lab? To address that issue I'll defer to a quote by the great Don Hacherl - you can think of him as the godfather of Active Directory.
These are by no means the only guides for securing AD or your Windows Servers. There are also good books and plenty of blogs and other guides. Please feel free to leave comments about your experiences with seucrity and AD
I also see questions come up all the time about people wanting to know how to secure their machines.
Although there is not one answer for every environment there are some good guidelines that have been released by Microsoft and various US Federal agencies that can help out.
In my opinion there are a handful of universal rules that apply to any Active Directory environment.
Limit the number of enterprise and domain administrators. I've seen plenty of organizations lock down their systems and take a lot of good security measures and then you look and there could be 50-100 (or more)domain admins.
Domain admins have control over every aspect of your domain, in fact a domain admin can have control of your entire forest.
It is important to limit these very powerful accounts. Limiting admins also limits the number of inadvertent mistakes that can cause issues
See Rule #1 :)
Don't give your users admin rights to their PCs. This seems like a no brainier but I was involved in a question on one of the boards recently and the admin's boss mandated that he make all the users admins on their machines.
So now you have limited admins and you have a good anti-virus program and are patching your servers with the appropriate patches.
What other guidelines are out there to help an admin secure AD and their servers?
The following is a list of some guides that should get most organizations going in the right direction
- NSA Security Guides
Yes the NSA does more than electronic and their security guides are really in depth
and have a lot of good information. - DISA Security Checklists
Defense Information System Agency (DISA) is another US Federal Agency. These checklists are similar to the NSA guides. - DISA Active Directory STIG
STIG's are DISA's Security Technical Implementation Guides and this one is particular to Active Directory. - Microsoft Best Practice Guide for Securing Active Directory
Microsoft's best practices for securing Active Directory - Microsoft Server 2003 Security Guide
Microsoft's guide on how to harden Windows Server 2003 - Microsoft Windows Server 2008 Security Guide
Similar to the 2003 guide but for 2008 - Federal Dektop Core Configuration (FDCC)
Although not for servers FDCC is a mandate for US Federal agencies and these lock downs can help all organizations.
UPDATE via comments from Garrett - Thanks Garrett!!
The Active Directory STIG has been deprecated by the all encompasing Directory Services STIG. While it has sections for specific software (like AD), it also contains overarching security guidlines that trancends all implementations of Directory Services.
http://iase.disa.mil/stigs/stig/directory-services-stig-v1r1.pdf
Those guides are a really good place to start if you want to learn more about securing your Windows Servers and AD Infrastructure.
This all leads me to Universal Rule #4...
Don't just blindly install security templates and don't lock down Active Directory or your servers without testing testing testing. This may seem like common sense but again I've seen many incidents of servers or AD being hardened and then users may lose functionality or other major problems can arise because the lock downs were not tested. It is important to be secure but at the end of the day it is also important for our users/customers to be able to function and do their jobs.
You say you don't have a test lab? To address that issue I'll defer to a quote by the great Don Hacherl - you can think of him as the godfather of Active Directory.
"You do, in fact, have a lab environment. What you do not have is a production environment."
These are by no means the only guides for securing AD or your Windows Servers. There are also good books and plenty of blogs and other guides. Please feel free to leave comments about your experiences with seucrity and AD
Labels:
Active Directory,
Security
Friday, April 24, 2009
Force Certain Users to change passwords via Command Line
There was a question that recently came up where the poster wanted to force some of his users whose login name started with B to change their passwords. He wanted to do this using the command line.
This Friday quick hitter post will show two ways to do this (there are other ways also)
What I like for this sort of task are adfind and admod by Joe Richards
The command I used was:
adfind -default -f "&(objectcategory=person)(objectclass=user)(samaccountname=b*)" -dsq | admod pwdLastSet::0

That will set "User must change password at next logon" for logon names that begin with B.
Some notes about this command:
Brandon Shell also came in with a powershell command to do this. If you don't know Brandon check out his blog . Brandon is very knowledgeable but also a really cool guy who is always willing to help and a huge asset to the community.
The powershell command takes advantage of Quest's Active Directory cmdlets. Big thanks to Dmitry Sotnikov and everyone at Quest for those.
The command is
Get-QADUser -SamAccountName b* | Set-QADUser -UserMustChangePassword $true

As you can see both commands worked and met the requirements. I hope you can also see how you can manipulate these commands to set other attributes for example. Comment or contact me for more info.
For those that are more comfortable with the GUI you can run the same LDAP query I used in adfind in Active Directory Users and Computers and find them and highlight them all at once and check the box to force them to change their password.
Hope everyone has a great weekend, spring is finally here on the East Coast of the USA so it should be nice.
This Friday quick hitter post will show two ways to do this (there are other ways also)
What I like for this sort of task are adfind and admod by Joe Richards
The command I used was:
adfind -default -f "&(objectcategory=person)(objectclass=user)(samaccountname=b*)" -dsq | admod pwdLastSet::0

That will set "User must change password at next logon" for logon names that begin with B.
Some notes about this command:
- Joe puts a lot of safety nets in his tools (good thing).
- You can use the -unsafe switch with admod if you don't want a safety or you can use the -safety switch and specify how many objects you want to modify (by default the safety kicks in at 10)
- You can also specify -upto xx if you want it to do xx object mods and then stop...thanks Joe for that one :)
Brandon Shell also came in with a powershell command to do this. If you don't know Brandon check out his blog . Brandon is very knowledgeable but also a really cool guy who is always willing to help and a huge asset to the community.
The powershell command takes advantage of Quest's Active Directory cmdlets. Big thanks to Dmitry Sotnikov and everyone at Quest for those.
The command is
Get-QADUser -SamAccountName b* | Set-QADUser -UserMustChangePassword $true

As you can see both commands worked and met the requirements. I hope you can also see how you can manipulate these commands to set other attributes for example. Comment or contact me for more info.
For those that are more comfortable with the GUI you can run the same LDAP query I used in adfind in Active Directory Users and Computers and find them and highlight them all at once and check the box to force them to change their password.
Hope everyone has a great weekend, spring is finally here on the East Coast of the USA so it should be nice.
Labels:
Active Directory,
adfind,
admod,
Powershell,
quick-hitters
Wednesday, April 22, 2009
Lessons Learned from Eric Fleischman
As previously mentioned I attended the Philly.NET users group Code Camp on Saturday 4/18/2009.
I had the great privilege to sit through two sessions from Eric Fleischman.
Who is Eric Fleischman you ask?
Eric is currently the Dev Lead for Virtualization(cloud services) at Microsoft. Eric has also been a lead developer on the AD team for Microsoft. When it comes to those that know AD the best there is no debate...Eric makes that list.
One of Eric's best known projects in the AD community was creating the largest Active Directory known to date.
What I wanted to do is list some of the things I picked up.
That was just a taste of what Eric talked about. If you ever get a chance to go see Eric speak then do it!! Eric lived up to his reputation and in fact he exceeded all expectations.
He could have a great career after Microsoft as a college professor or high school teacher if he wanted to. Very smart but also good at conveying his thoughts and ideas to the audience. I can't imagine anyone not giving him a 5/5 on any evaluation.
I had the great privilege to sit through two sessions from Eric Fleischman.
Who is Eric Fleischman you ask?
Eric is currently the Dev Lead for Virtualization(cloud services) at Microsoft. Eric has also been a lead developer on the AD team for Microsoft. When it comes to those that know AD the best there is no debate...Eric makes that list.
One of Eric's best known projects in the AD community was creating the largest Active Directory known to date.
What I wanted to do is list some of the things I picked up.
- Always make every DC a GC, assume you can do that unless you can prove that your bandwidth can't handle it. In most environments the DC/GC role will be fine. We already do this where I am but I was glad to hear Eric recommend it.
- Leave Field Engineering Logging on everywhere. Turning it on won't hurt perf and the info you get from it is very valuable. It will let you know about inefficient and expensive queries in your environment. More info on field engineering can be found here We currently don't have this on but we soon will turn it on.
- Eric considers Replication and Query Optimization the hardest part of AD. You also have to know that Eric works with very large implementations.
- Don't ever user eseutil to repair your AD database. Never even tried that one in production and will never try it :)
- Establish baselines: run SPA from time to time and run Perfmon a lot.
- Collect Crash dumps and look at your own dumps before asking PSS.
- The following commands will help with the crash dumps before calling PSS.
- windbg –z foo.dmp
- sympath SRV*http://msdl.microsoft.com/download/symbols
- !analyze -v
- windbg –z foo.dmp
That was just a taste of what Eric talked about. If you ever get a chance to go see Eric speak then do it!! Eric lived up to his reputation and in fact he exceeded all expectations.
He could have a great career after Microsoft as a college professor or high school teacher if he wanted to. Very smart but also good at conveying his thoughts and ideas to the audience. I can't imagine anyone not giving him a 5/5 on any evaluation.
Labels:
Active Directory,
AD Legends,
Miscellaneous
Happy Earth Day, Microsoft Style
Today is April 22, 2009 which is Earth Day and while most of us are concerned about our environment and the future of our planet there are some real things that we as admin/engineers can do to help.
What I'm going to talk about today is using the power options with group policy preferences.
I won't go in-depth into the background of group policy preferences. Group Policy MVP Darren Mar-Elia has a great white paper titled Group Policy Preferences Overview I encourage anyone new to preferences to check that out.
As Darren mentions in the paper you may need to install Client Side Extensions (CSEs). You can get those CSEs for various operating systems from Microsoft.
At this point I'm assuming you are ready to go for Group Policy Preferences.
The power options are located in both the computer configuration or user configuration nodes.
If you set the options in both locations then the user setting will win as the user settings are configured after the computer settings.
The computer power options are located in:
Computer Configuration | Preferences | Control Panel Settings | Power Options
The user power options are located in:
User Configuration | Preferences | Control Panel Settings | Power Options
We have now decided to help the planet and setup some user power options. I'll create a new GPO called Happy Earth Day - Power Options
You can set a new Power Options and/or a new Power Scheme by right clicking and selecting New

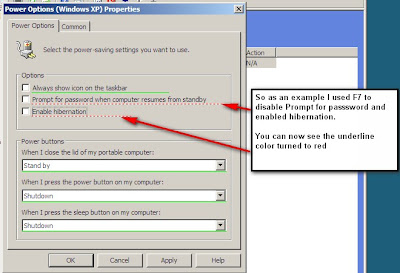
I'll first go into power options, you can set several options including enabling hibernation.
You can also set the behavior when the power button is pressed.
The power button options for closing the lid of a portable computer/laptop are:
The power button options for pressing the power button or sleep button on a computer are:
You can view the power options tab here:
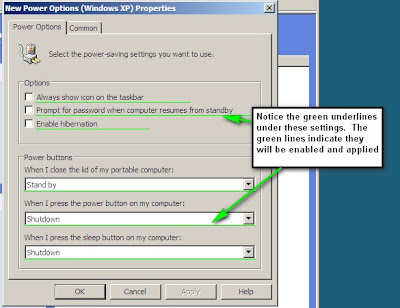
One important thing to note are the green underlines. That indicates that the setting is enabled and will be applied.
The group policy team at Microsoft had a very good series explaining this:
Part one: Red/Green GP Preferences
Part Two: Red/Green Underlining Continued
As you can see in the Group Policy team posts you can use F5, F6, F7, or F8 to configure these settings
Here is an example:
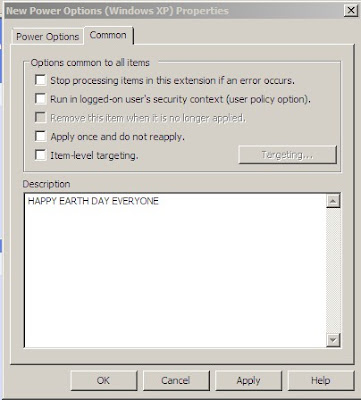
The common tab allows to to configure other options including item level targeting
Next we will move on to a new Power Scheme -- this is where we can really make a difference on Earth Day.
With the Power Scheme you can select an action
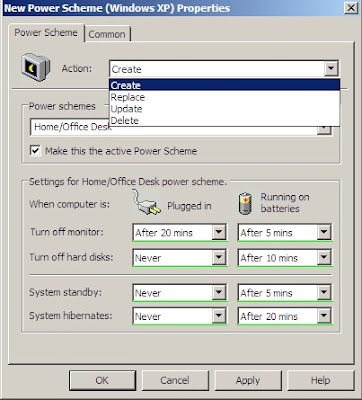
Those actions include Create, Delete, Replace, and Update
As you can see you can define when to turn off monitors and disks and when to put the system into standby or hibernate.
So the obvious question is What are some recommended settings?
The EPA recommends setting computers to enter system standby or hibernate after 30 to 60 minutes of inactivity. To save even more, set monitors to enter sleep mode after 5 to 20 minutes of inactivity. Obviously the lower the setting, the more energy you save.
The department of energy has also released EZ GPO for those that may not be using preferences yet.
As with any group policy test it out first in a lab and then pilot users.
It may not seem like this could make a big difference on the environment but think if every admin across the world enabled power saving schemes....again we can all do our part and hopefully help the planet.
HAPPY EARTH DAY 2009 EVERYONE!!!
What I'm going to talk about today is using the power options with group policy preferences.
I won't go in-depth into the background of group policy preferences. Group Policy MVP Darren Mar-Elia has a great white paper titled Group Policy Preferences Overview I encourage anyone new to preferences to check that out.
As Darren mentions in the paper you may need to install Client Side Extensions (CSEs). You can get those CSEs for various operating systems from Microsoft.
At this point I'm assuming you are ready to go for Group Policy Preferences.
The power options are located in both the computer configuration or user configuration nodes.
If you set the options in both locations then the user setting will win as the user settings are configured after the computer settings.
The computer power options are located in:
Computer Configuration | Preferences | Control Panel Settings | Power Options
The user power options are located in:
User Configuration | Preferences | Control Panel Settings | Power Options
We have now decided to help the planet and setup some user power options. I'll create a new GPO called Happy Earth Day - Power Options
You can set a new Power Options and/or a new Power Scheme by right clicking and selecting New

I'll first go into power options, you can set several options including enabling hibernation.
You can also set the behavior when the power button is pressed.
The power button options for closing the lid of a portable computer/laptop are:
- Do Nothing
- Stand by
- Hibernate
The power button options for pressing the power button or sleep button on a computer are:
- Do nothing
- Ask me what to do
- Stand by
- Shutdown
- Hibernate
You can view the power options tab here:

One important thing to note are the green underlines. That indicates that the setting is enabled and will be applied.
The group policy team at Microsoft had a very good series explaining this:
Part one: Red/Green GP Preferences
Part Two: Red/Green Underlining Continued
As you can see in the Group Policy team posts you can use F5, F6, F7, or F8 to configure these settings
- F5 = Configure all these settings
- F6 = Configure just this setting - this is an individual setting
- F7 = Ignore just this setting - this is an individual setting
- F8 = Ignore all these settings
Here is an example:

The common tab allows to to configure other options including item level targeting

Next we will move on to a new Power Scheme -- this is where we can really make a difference on Earth Day.
With the Power Scheme you can select an action

Those actions include Create, Delete, Replace, and Update
- Create - Create a newly configured Power Scheme. If a power scheme with the same name as the Power Scheme item exists, then the existing Power Scheme is not modified.
- Delete - Remove a Power Scheme with the same name as the Power Scheme preference item. The extension performs no action if the Power Scheme does not exist.
- Replace - Delete and recreate the named power scheme. The net result of the Replace action overwrites all existing settings associated with the power scheme. If the power scheme does not exist, then the Replace action creates a newly configured power scheme.
- Update - Modify a power scheme. The action differs from Replace in that it updates the settings defined within the preference item. All other settings remain as they were previously configured. If the power scheme does not exist, then the Update action creates a new power scheme.
As you can see you can define when to turn off monitors and disks and when to put the system into standby or hibernate.
So the obvious question is What are some recommended settings?
The EPA recommends setting computers to enter system standby or hibernate after 30 to 60 minutes of inactivity. To save even more, set monitors to enter sleep mode after 5 to 20 minutes of inactivity. Obviously the lower the setting, the more energy you save.
The department of energy has also released EZ GPO for those that may not be using preferences yet.
As with any group policy test it out first in a lab and then pilot users.
It may not seem like this could make a big difference on the environment but think if every admin across the world enabled power saving schemes....again we can all do our part and hopefully help the planet.
Labels:
Active Directory,
GPP,
Group Policy
Tuesday, April 21, 2009
Active Directory Masters Course - Caution Ahead
Last weekend I attended a day long event sponsored by the philly.NET users group
There were a lot of sessions for coders and developers. Laura Hunter put together a really great lineup of speakers (Eric Fleischman, Brandon Shell, Mark Arnold, & Gil Kirkpatrick) for the Active Directory/IT Pro crowd.
After one of the sessions my friend Eric and I were talking to one of the instructors and a guy in class who had just come back from the AD Masters Course/Cert Program
What he told us is that only 10 out of 21 people in his class passed. In the previous track only 1 out of 21 passed. The instructor/MVP also backed the point of the exams being tough. I don't know if those numbers are dead on but even if they are a little off I got the point...not an easy cert to get.
What I think is happening is that the AD Masters course covers so much ground and there are not that many positions that allow someone to work with all the technologies needed to pass the exam. For example in my case ADRMS and ADFS would be big challenges.
I think what needs to happen is a mind set change for those going to take this course and exam. The windows/AD guys/gals have to treat this like Cisco folks treat the CCIE. That means setup a very good lab and just test test test and try to know the stuff cold before you go to the course. So in my case I'd really dig into ADFS and ADRMS and do a lot of brushing up on everything else.
I think it is good that they are making it this challenging. Other Microsoft certs have gotten a bad reputation over the years so it looks like this the masters cert is not going to have the same stigma. Also if in 5 years the Masters takes hold like the CCIE has then that will be very beneficial ($$$) for those that hold this cert/title.
I'm not sure if I'll ever go(it is not cheap) but now I know that I have a lot of work to do if I ever decide to go
There were a lot of sessions for coders and developers. Laura Hunter put together a really great lineup of speakers (Eric Fleischman, Brandon Shell, Mark Arnold, & Gil Kirkpatrick) for the Active Directory/IT Pro crowd.
After one of the sessions my friend Eric and I were talking to one of the instructors and a guy in class who had just come back from the AD Masters Course/Cert Program
What he told us is that only 10 out of 21 people in his class passed. In the previous track only 1 out of 21 passed. The instructor/MVP also backed the point of the exams being tough. I don't know if those numbers are dead on but even if they are a little off I got the point...not an easy cert to get.
What I think is happening is that the AD Masters course covers so much ground and there are not that many positions that allow someone to work with all the technologies needed to pass the exam. For example in my case ADRMS and ADFS would be big challenges.
I think what needs to happen is a mind set change for those going to take this course and exam. The windows/AD guys/gals have to treat this like Cisco folks treat the CCIE. That means setup a very good lab and just test test test and try to know the stuff cold before you go to the course. So in my case I'd really dig into ADFS and ADRMS and do a lot of brushing up on everything else.
I think it is good that they are making it this challenging. Other Microsoft certs have gotten a bad reputation over the years so it looks like this the masters cert is not going to have the same stigma. Also if in 5 years the Masters takes hold like the CCIE has then that will be very beneficial ($$$) for those that hold this cert/title.
I'm not sure if I'll ever go(it is not cheap) but now I know that I have a lot of work to do if I ever decide to go
Labels:
Active Directory,
Certification
Thursday, April 16, 2009
Security Filtering and Group Policy
One of the questions I often see is how do I only apply group policies to certain groups or users or computers.
...for those of you already familiar with group policy you will know this already. This post is for those new to working with group policies. If you were sent here by a question I participated in then feel leave a comment if this helps you out.
This entry will serve to supplement Microsoft's article http://technet.microsoft.com/en-us/library/cc781988.aspx
I will first assume you are using GPMC to manage your group policies.
First thing is that group policies can't be applied directly to groups. You link a group policy at the site, domain, or OU level. The policies apply to either users and/or computers.
So suppose you have a policy that you only want to apply to a subset of users or computers. The first thing is to create a group and place the users or computers you want this policy to apply to into that group (I'll use a global group in this example). We will call that group testgroup1.
In GPMC select your group policy object. In GPMC you will see the Scope tab. Notice that by default the policy will apply to Authenticated Users

You will remove authenticated users. Then you can add your testgroup1. Now the policy will only be applied to your testgroup1

So what really happens in the background when you make that change?
If you go to the delegation tab you will see an Advanced button.


As you can see testgroup1 now has "read" and "Apply Group Policy" set to Allow. So the policy will apply to that group. Read and Apply group policy are both needed in order for the user or computer to receive and process the policy
...at this point some of you may be asking, what if I wanted to "deny" the policy to a group or user. If you instincts tell you to apply set Read & Apply Group Policy to "deny" then you would be correct.
In the following screenshot I've set deny permissions for Read & Apply Group Policy and testgroup1 will not receive the policy.

That is really all there is to security filtering and group policies...not so hard after all. Please feel free to contact me if you have any questions about this.
Thanks
Mike
...for those of you already familiar with group policy you will know this already. This post is for those new to working with group policies. If you were sent here by a question I participated in then feel leave a comment if this helps you out.
This entry will serve to supplement Microsoft's article http://technet.microsoft.com/en-us/library/cc781988.aspx
I will first assume you are using GPMC to manage your group policies.
First thing is that group policies can't be applied directly to groups. You link a group policy at the site, domain, or OU level. The policies apply to either users and/or computers.
So suppose you have a policy that you only want to apply to a subset of users or computers. The first thing is to create a group and place the users or computers you want this policy to apply to into that group (I'll use a global group in this example). We will call that group testgroup1.
In GPMC select your group policy object. In GPMC you will see the Scope tab. Notice that by default the policy will apply to Authenticated Users

You will remove authenticated users. Then you can add your testgroup1. Now the policy will only be applied to your testgroup1

So what really happens in the background when you make that change?
If you go to the delegation tab you will see an Advanced button.


As you can see testgroup1 now has "read" and "Apply Group Policy" set to Allow. So the policy will apply to that group. Read and Apply group policy are both needed in order for the user or computer to receive and process the policy
...at this point some of you may be asking, what if I wanted to "deny" the policy to a group or user. If you instincts tell you to apply set Read & Apply Group Policy to "deny" then you would be correct.
In the following screenshot I've set deny permissions for Read & Apply Group Policy and testgroup1 will not receive the policy.

That is really all there is to security filtering and group policies...not so hard after all. Please feel free to contact me if you have any questions about this.
Thanks
Mike
Labels:
Active Directory,
Group Policy
UGLY & ADGLP what are they?
You will often hear the acronyms UGLY and AGDLP when people are talking about how to apply permissions to resources (usually in the context of files/folders) in an Active Directory environment.
There are three types of security groups in Active Directory they are
• Universal
• Global
• Domain Local
More information on the scope of these groups can be found here:
http://technet.microsoft.com/en-us/library/cc755692.aspx
As you can see you can nest global groups into domain local groups and that is where these acronyms come into play
AGDLP = Accounts into globals, Globals into Domain Locals, assign Permissions
UGLY = Users into global groups, Global into domain Local groups, You assign permissions
NOTE: You will also hear AGLP refered to as AGDLP
So the question comes up should this method always be used when assigning permissions?
If you are in a single domain forest or if you are using an empty root design then you don’t need to worry about either of these acronyms. You can just use globals or domain locals and add members and apply permissions. Don’t worry about nesting groups.
In a multi-domain forest the thought process behind AGLP and UGLY is that you only ever add members to the global groups. From the link above you can see that
The one issue that can come up is that you may lose some control of who has access to the resources unless you have a good auditing process setup.
Suppose you have a North America, Asia, Europe, & South America domain. Now in the North America domain you have an Accounting folder and you use AGLP/UGLY to apply permissions. If you are only an admin in North America then the admins from all the other domains could be adding members to their global groups that may not really need access.
So as you can see there are pros and cons to the various methods. The final answer here is that there is no set in stone hard and fast answer. You have to look at your organization/structure/environment and decide what is best for you
There are three types of security groups in Active Directory they are
• Universal
• Global
• Domain Local
More information on the scope of these groups can be found here:
http://technet.microsoft.com/en-us/library/cc755692.aspx
As you can see you can nest global groups into domain local groups and that is where these acronyms come into play
AGDLP = Accounts into globals, Globals into Domain Locals, assign Permissions
UGLY = Users into global groups, Global into domain Local groups, You assign permissions
NOTE: You will also hear AGLP refered to as AGDLP
So the question comes up should this method always be used when assigning permissions?
If you are in a single domain forest or if you are using an empty root design then you don’t need to worry about either of these acronyms. You can just use globals or domain locals and add members and apply permissions. Don’t worry about nesting groups.
In a multi-domain forest the thought process behind AGLP and UGLY is that you only ever add members to the global groups. From the link above you can see that
because groups with global scope are not replicated outside their own domain, you can change accounts in a group having global scope frequently without generating replication traffic to the global catalog.
The one issue that can come up is that you may lose some control of who has access to the resources unless you have a good auditing process setup.
Suppose you have a North America, Asia, Europe, & South America domain. Now in the North America domain you have an Accounting folder and you use AGLP/UGLY to apply permissions. If you are only an admin in North America then the admins from all the other domains could be adding members to their global groups that may not really need access.
So as you can see there are pros and cons to the various methods. The final answer here is that there is no set in stone hard and fast answer. You have to look at your organization/structure/environment and decide what is best for you
Labels:
Active Directory,
permissions
Tuesday, April 14, 2009
How great are Special Forces!!
Taking a detour from Active Directory.
By now everyone has heard how the Navy Seals rescued Captain Phillips from the pirates off the coast of Africa.
For those that don't know the three Navy Seals parachuted in and watched the boat Captain Phillips was in for several days. Then at one point two of the pirates briefly stuck their head out and two seals took simultaneous shots and killed the two pirates. The third seal at the same time shot at the third pirate inside (there must have been a window). That third shot was sucessful too. Three simultaneous shots...three kills. NBC News had a really great animation of all this but I can't find it on the web. If I do find it I'll post it.
Update from my friend Keith (also an Army Vet)
Great info Keith!! This is even more impressive.
How bad ass is that? Man oh man these guys are good. Just think if one shot would have been off Captain Phillips would have been a dead man.
I was in the Army but never came anywhere close to doing anything this high speed. You just have to take your hat off to all these guys in Special Forces they are a rare breed and we owe them a lot of thanks!!
Navy Seals, Army Rangers/Green Berets/Delta Force, USMC Force Recon, England’s SAS, Israeli Sayeret, and Germany's KSK.
Thanks to all of you, most of us will never know all the missions and things you all do to keep the world safe because of how Top Secret your missions are but we know you are out there and we know you are doing great things so THANK YOU!!!
Hooooaaahhh!!
By now everyone has heard how the Navy Seals rescued Captain Phillips from the pirates off the coast of Africa.
For those that don't know the three Navy Seals parachuted in and watched the boat Captain Phillips was in for several days. Then at one point two of the pirates briefly stuck their head out and two seals took simultaneous shots and killed the two pirates. The third seal at the same time shot at the third pirate inside (there must have been a window). That third shot was sucessful too. Three simultaneous shots...three kills. NBC News had a really great animation of all this but I can't find it on the web. If I do find it I'll post it.
Update from my friend Keith (also an Army Vet)
It was night and they used thermal image scopes that way they could see heat through the fiberglass life boat. 3 shots 3 kills. The forth pirate was aboard the navy ship as a negotiator
Great info Keith!! This is even more impressive.
How bad ass is that? Man oh man these guys are good. Just think if one shot would have been off Captain Phillips would have been a dead man.
I was in the Army but never came anywhere close to doing anything this high speed. You just have to take your hat off to all these guys in Special Forces they are a rare breed and we owe them a lot of thanks!!
Navy Seals, Army Rangers/Green Berets/Delta Force, USMC Force Recon, England’s SAS, Israeli Sayeret, and Germany's KSK.
Thanks to all of you, most of us will never know all the missions and things you all do to keep the world safe because of how Top Secret your missions are but we know you are out there and we know you are doing great things so THANK YOU!!!
Hooooaaahhh!!
Labels:
Army Hooaahh
Modify User displayName using the command line
A question came up in the forums today about how to modify the displayname of users to Lastname, Firstname
My friend Matt had a very good suggestion and that was to use a tool called ADModify.NET
ADModify is indeed a great tool and will do that job and that is a very good recommendation, but what I'll show here is a command line method using Joe Richard's adfind and admod tools...have I mentioned I'm a big fan of these tools :)
The first thing to know is that in Active Directory the Lastname and Firstname attributes are not stored that way. What they really are in the background is:
Lastname = sn
Firstname = givenName
So for this example what I'll show is the before, the modification, then the after
What I'll run first is just an adfind command to show that the displayName field is not populated
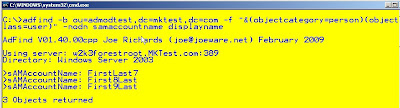
As you can see no displayName
Next I will use adfind and pipe those results into admod...that is what makes these tools very very powerful
The command is (my accounts are in an OU called admodtest)
adfind -b ou=admodtest,dc=mktest,dc=com -f "&(objectcategory=person)(objectclass=user)" sn givenname -adcsv | admod "displayname::{{sn}}, {{givenname}}"
If you have more than 10 to change at once you can use the -unsafe switch in admod (default will change 10...joe puts a lot of safety nets into his tools)
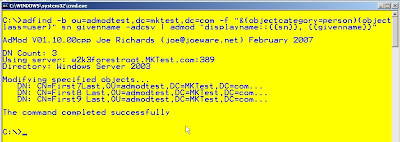
Note: the -adcsv is a switch that joe has put in so that the output can be passed to his other tools (admod in this case)
The command did complete successfully, but now I run the same adfind command to make sure the display name is what I want...and it works as advertised.
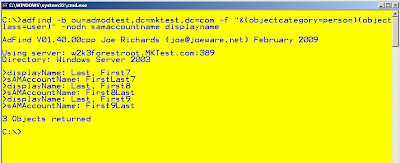
There are also other command line methods (dsmod from Microsoft, PowerShell, VBScript, etc...)
This is just one option in addition to ADModify.NET
My friend Matt had a very good suggestion and that was to use a tool called ADModify.NET
ADModify is indeed a great tool and will do that job and that is a very good recommendation, but what I'll show here is a command line method using Joe Richard's adfind and admod tools...have I mentioned I'm a big fan of these tools :)
The first thing to know is that in Active Directory the Lastname and Firstname attributes are not stored that way. What they really are in the background is:
Lastname = sn
Firstname = givenName
So for this example what I'll show is the before, the modification, then the after
What I'll run first is just an adfind command to show that the displayName field is not populated

As you can see no displayName
Next I will use adfind and pipe those results into admod...that is what makes these tools very very powerful
The command is (my accounts are in an OU called admodtest)
adfind -b ou=admodtest,dc=mktest,dc=com -f "&(objectcategory=person)(objectclass=user)" sn givenname -adcsv | admod "displayname::{{sn}}, {{givenname}}"
If you have more than 10 to change at once you can use the -unsafe switch in admod (default will change 10...joe puts a lot of safety nets into his tools)

Note: the -adcsv is a switch that joe has put in so that the output can be passed to his other tools (admod in this case)
The command did complete successfully, but now I run the same adfind command to make sure the display name is what I want...and it works as advertised.

There are also other command line methods (dsmod from Microsoft, PowerShell, VBScript, etc...)
This is just one option in addition to ADModify.NET
Labels:
Active Directory,
adfind,
admod
Monday, April 13, 2009
When were my domains created - quick-hitters
This will be the first post in what I'll call "quick-hitters". Short to the point posts to accomplish a specific task.
So you want to find a quick way to know when the domains in your forest were created.
This is where I really like a tool called ADFIND by Active Directory MVP Joe Richards. Joe is one of my favorite people in the AD world. Really smart but also a cool guy that is always willing to help.
The command is
adfind -gcb -f objectcategory=domain name whencreated -tdcgt

In my example screen shot I only have one domain in that forest in my lab but it works across your forest becasue of the -gcb switch. If you only want to search your domain you can replace -gcb with -default.
Thanks
Mike
So you want to find a quick way to know when the domains in your forest were created.
This is where I really like a tool called ADFIND by Active Directory MVP Joe Richards. Joe is one of my favorite people in the AD world. Really smart but also a cool guy that is always willing to help.
The command is
adfind -gcb -f objectcategory=domain name whencreated -tdcgt

In my example screen shot I only have one domain in that forest in my lab but it works across your forest becasue of the -gcb switch. If you only want to search your domain you can replace -gcb with -default.
Thanks
Mike
Labels:
Active Directory,
adfind,
quick-hitters
Sunday, April 12, 2009
Need AD DSRM Password -- Not So Fast
The situation was that the network team was Re-IPing a subnet and before that was done the IP of the domain controller was not changed. At the time the new subnet could not contact the subnet where the DNS server was located.
There were calls made and eventually I was called on the subject. I was called in order to provide the AD Directory Services Restore Mode (DSRM) password. The plan was apparently to log into the domain controller hit F8 during boot go into DSRM and modify the IP address.
After thinking about it and talking it over with my good friend Eric Jansen[1] we thought that was overkill. The domain controller has a writable copy of AD. In this situation there shouldn't be any problems logging in at the DC, regardless of some peoples' concerns about DNS client side settings.
This of course called for a test and this is very easy to setup in a virtual environment.
In my main domain I have three domain controllers (2 Windows 2003 and 1 Windows 2008). For this test I changed W2K3 DC2 and had it only point to DC1 for DNS. I created a new account and turned off DC1.

As you can see in the screen shot, the DC only has one DNS server configured and that server is off/not responding. This would be a problem if this were a workstation but this test was just for a domain controller. The workstation issue will be explained in a future entry.
The next step was to try and log into the box. As expected the login went fine and I was authenticated and was able to change the IP on the box.
DSRM mode password not needed --- crisis averted.
Thanks
Mike
[1] Out of all the people that I've worked with Eric is the best and my favorite person to work with not only because he is smart but because he really enjoys and has a passion for AD. Watch for Eric's blog on my blog list...when he creates it. Ok sure Eric has a wife and young daughter and in college full time so he may not have as much time as I do....no excuses Eric :)
There were calls made and eventually I was called on the subject. I was called in order to provide the AD Directory Services Restore Mode (DSRM) password. The plan was apparently to log into the domain controller hit F8 during boot go into DSRM and modify the IP address.
After thinking about it and talking it over with my good friend Eric Jansen[1] we thought that was overkill. The domain controller has a writable copy of AD. In this situation there shouldn't be any problems logging in at the DC, regardless of some peoples' concerns about DNS client side settings.
This of course called for a test and this is very easy to setup in a virtual environment.
In my main domain I have three domain controllers (2 Windows 2003 and 1 Windows 2008). For this test I changed W2K3 DC2 and had it only point to DC1 for DNS. I created a new account and turned off DC1.

As you can see in the screen shot, the DC only has one DNS server configured and that server is off/not responding. This would be a problem if this were a workstation but this test was just for a domain controller. The workstation issue will be explained in a future entry.
The next step was to try and log into the box. As expected the login went fine and I was authenticated and was able to change the IP on the box.
DSRM mode password not needed --- crisis averted.
Thanks
Mike
[1] Out of all the people that I've worked with Eric is the best and my favorite person to work with not only because he is smart but because he really enjoys and has a passion for AD. Watch for Eric's blog on my blog list...when he creates it. Ok sure Eric has a wife and young daughter and in college full time so he may not have as much time as I do....no excuses Eric :)
Labels:
Active Directory,
DSRM
Saturday, April 11, 2009
My Favorite Commercial of All-Time
Michael Jordan is my favorite athlete of all time. I really loved watching him play and watch that passion he had for the game.
What I really loved about this commercial is that Michael shows us all that even he has failed many many times…but in the end that is why he succeeded.
This is the same with Active Directory. We often try new things or maybe fail to solve the issue at hand in the first try or within the first few minutes….but that is why we succeed.
Labels:
Miscellaneous
Odd Title For your Blog – Is AD really fun?
So why would I call my blog “ADisFUN”. There are a lot of things in this world that people consider fun and Active Directory is not often mentioned in that list.
What I really enjoy is that AD fits about any network. From those small businesses that run AD using SBS or to the large companies that span the globe with thousands and thousands of users across multiple continents. That means knowing AD and how it works is needed everywhere.
There is also always something to learn which is probably the most fun I have. If you ever hear anyone tell you that they have completely mastered AD and know everything about it then that person is lying. There are always new features and new versions coming out. Microsoft constantly strives to improve AD and now that they are releasing new features every two years there is always more to learn and know and try to master.
An analogy I use is that I compare Active Directory to the game of golf. Golf can be a humbling game and even someone as great as Tiger Woods knows that he will never truly “master” the game. Tiger comes close but he learns new things about his game and golf all the time. This is the same with Active Directory. There are those in the AD world that I consider the “Tiger Woods of AD” and the great thing is those people will readily admit that they still have things to learn and master.
There are new issues we encounter on a regular basis and solving those issues is what I consider Fun. Learning the new features is what I consider Fun. Working with great people in the AD community (see my blog list for some examples) is what I consider Fun. Helping answer questions in the community and receiving emails or comments from people is very fun and rewarding.
…and yes even going out and getting new certifications every few years is what I consider Fun :)
What I really enjoy is that AD fits about any network. From those small businesses that run AD using SBS or to the large companies that span the globe with thousands and thousands of users across multiple continents. That means knowing AD and how it works is needed everywhere.
There is also always something to learn which is probably the most fun I have. If you ever hear anyone tell you that they have completely mastered AD and know everything about it then that person is lying. There are always new features and new versions coming out. Microsoft constantly strives to improve AD and now that they are releasing new features every two years there is always more to learn and know and try to master.
An analogy I use is that I compare Active Directory to the game of golf. Golf can be a humbling game and even someone as great as Tiger Woods knows that he will never truly “master” the game. Tiger comes close but he learns new things about his game and golf all the time. This is the same with Active Directory. There are those in the AD world that I consider the “Tiger Woods of AD” and the great thing is those people will readily admit that they still have things to learn and master.
There are new issues we encounter on a regular basis and solving those issues is what I consider Fun. Learning the new features is what I consider Fun. Working with great people in the AD community (see my blog list for some examples) is what I consider Fun. Helping answer questions in the community and receiving emails or comments from people is very fun and rewarding.
…and yes even going out and getting new certifications every few years is what I consider Fun :)
Labels:
Active Directory,
Miscellaneous
Subscribe to:
Posts (Atom)










