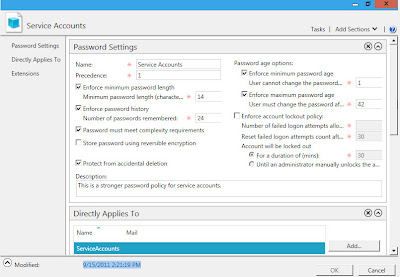
This entry is about a new feature in Windows Server 8. The ability to turn on and turn off the graphical shell.
Prior to Windows 2008 there was no Windows OS that didn't feature a full GUI. Linux folks would often criticize Windows admins for not being talented around the command line. That was true to some extent but there are a lot of Windows admins/engineers who are comfortable around the command line but there were tasks that could only be done via the GUI or were much easier from the GUI.
In Windows 2008 a new feature was introduced called server core
The Server Core installation option is an option that you can use for installing Windows Server 2008 A Server Core installation provides a minimal environment for running specific server roles, which reduces the maintenance and management requirements and the attack surface for those server roles
Server core was intimidating to a lot of Windows admins not used to administrating or configuring servers from the command line.
Server core was also available in 2008 R2 and introduced a tool called sconfig which made configuration much easier. Other features such as powershell were also added in 2008 R2.
There was no way to convert a server core to a full server if there was a feature that needed to be installed that core didn't support. I'm not sure what the server core adoption rate was. I've seen people speculate 10-15% but have not seen official numbers from Microsoft.
There are a lot of beneifts to server core including greatly reducing the number of reboots and patches needed. MVP Brian McCann has an excellent blog entry on Server Core with stats.
“In some cases, customers can see up to a 60% reduction in patch requirements and the number of reboots on a monthly basis” These are the numbers that back up statements such as that.Server core is still an option in Windows Server 8.
However for those that still are not comfortable with core there is an option to remove the GUI from a full installation of Windows 8.
As Ned Pyle pointed out in the comments of this AskDS blog this feature is not quite server core. Meaning using these steps doesn't turn your server into core but it does remove many of the GUI features. You will no longer need to worry about admins surfing the internet from your servers. This may end up being the preferred method for deploying Windows Server 8....time will tell.
I first noticed the Server Graphical Shell in the Features list in Windows Server 8. I had not seen this feature in the past.
The feature can be removed by just clearing the check box in the roles and features wizard from server manager.
I've unchecked the box in order to remove the Graphical Shell.
After the server is rebooted and comes back up the GUI shell is gone. Server manager is still available. Things like the MetroUI are now gone.
For fun I tried to surf the net using Internet Explorer
Suppose an admin later decides later that they want this feature back. It is just as easy as removing except this time the box is checked to add the feature
After a reboot the GUI shell is back.
For those that prefer PowerShell this can also be done in a few lines via PowerShell
I import the server manager module and viewed the features (not required)
From there it is as simple as remove-windowsfeature server-gui-shell
Adding it is just as easy...you guessed it
add-windowsfeature Server-Gui-Shell
Again I'd like to hear comments on this feature. Was it needed since we already have server core or is this a nice middle ground that will be widely adopted?
Thanks for reading.